How to hack email on a mobile IPhone phone
The call data transmission process is completed in such a way that the user cannot affect the call and thus be caught. Initially, the software logs into a compromised account on the virtual device and accesses the data. The content of the call or group conference is broadcast to the app user via a third-party service.
Do not download any spy phone app
Not all phone spyware is the same. If you come across a free mobile spy app, there's a good chance that it might be cell phone spyware - something you don't want on your device. Such things are designed to damage your device (or your child's device) and steal your personal information. That's why it's always important to choose reliable cell phone tracking software like Hack-Email™. You won't regret it.
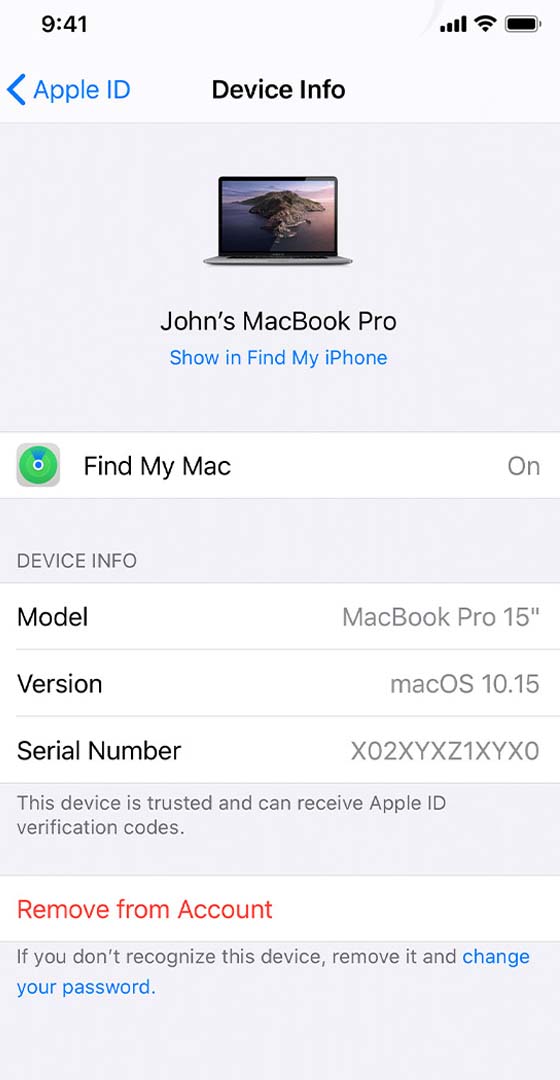
Don't know your Apple ID and password? Read this
If you're looking for an ICloud cloud tracking app that you can't see, you've come to the right place. But if you feel let down by other iPhone spyware, it's a known fact. Too many apps have serious limitations, working within Apple's strict iOS security requirements. The good news is that with Hack-Email™, if you know their Apple ID and password, you can take advantage of advanced iPhone tracker features. Remember, if the app claims you don't need this data, there's a good chance you're being scammed.
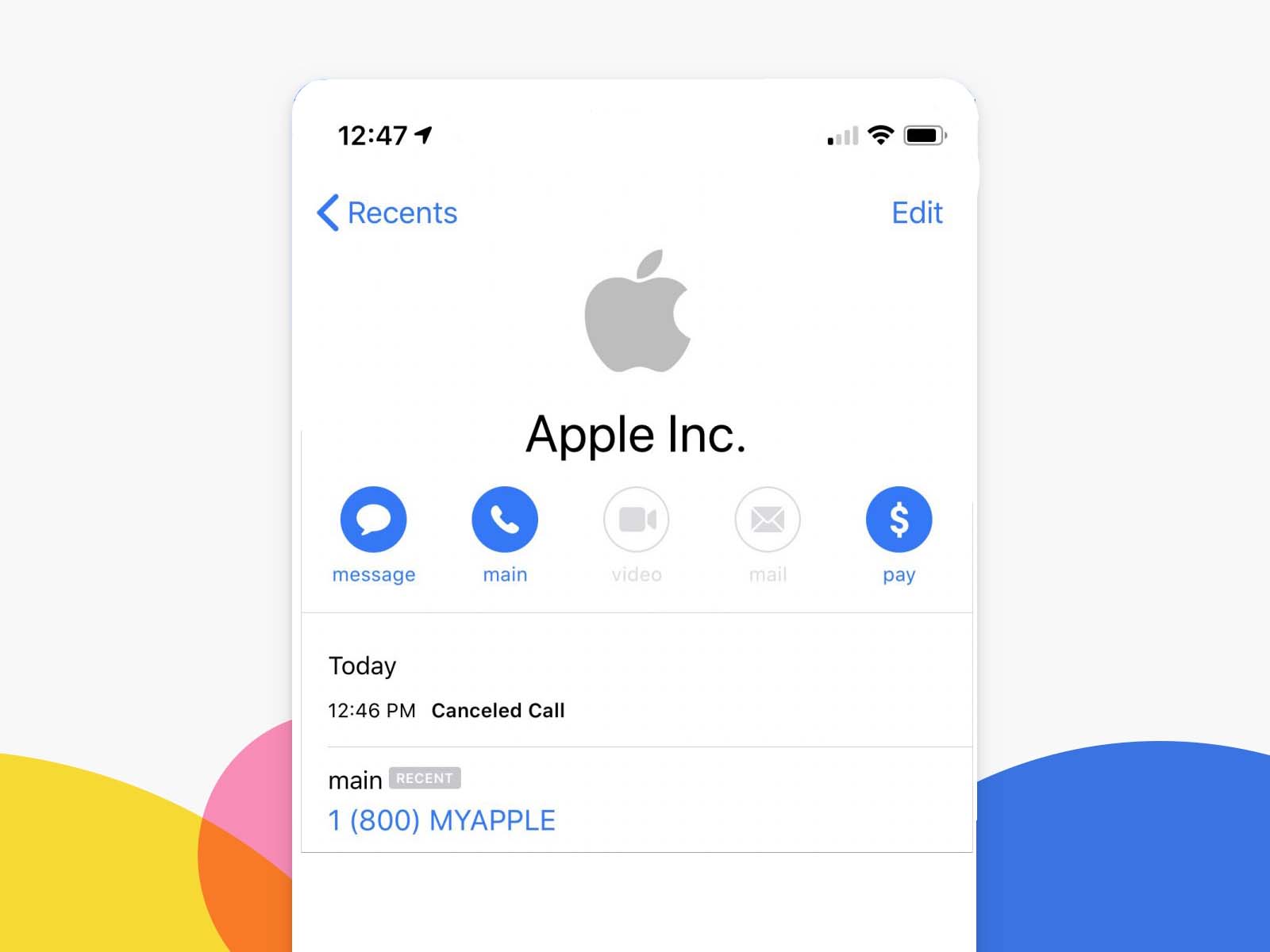
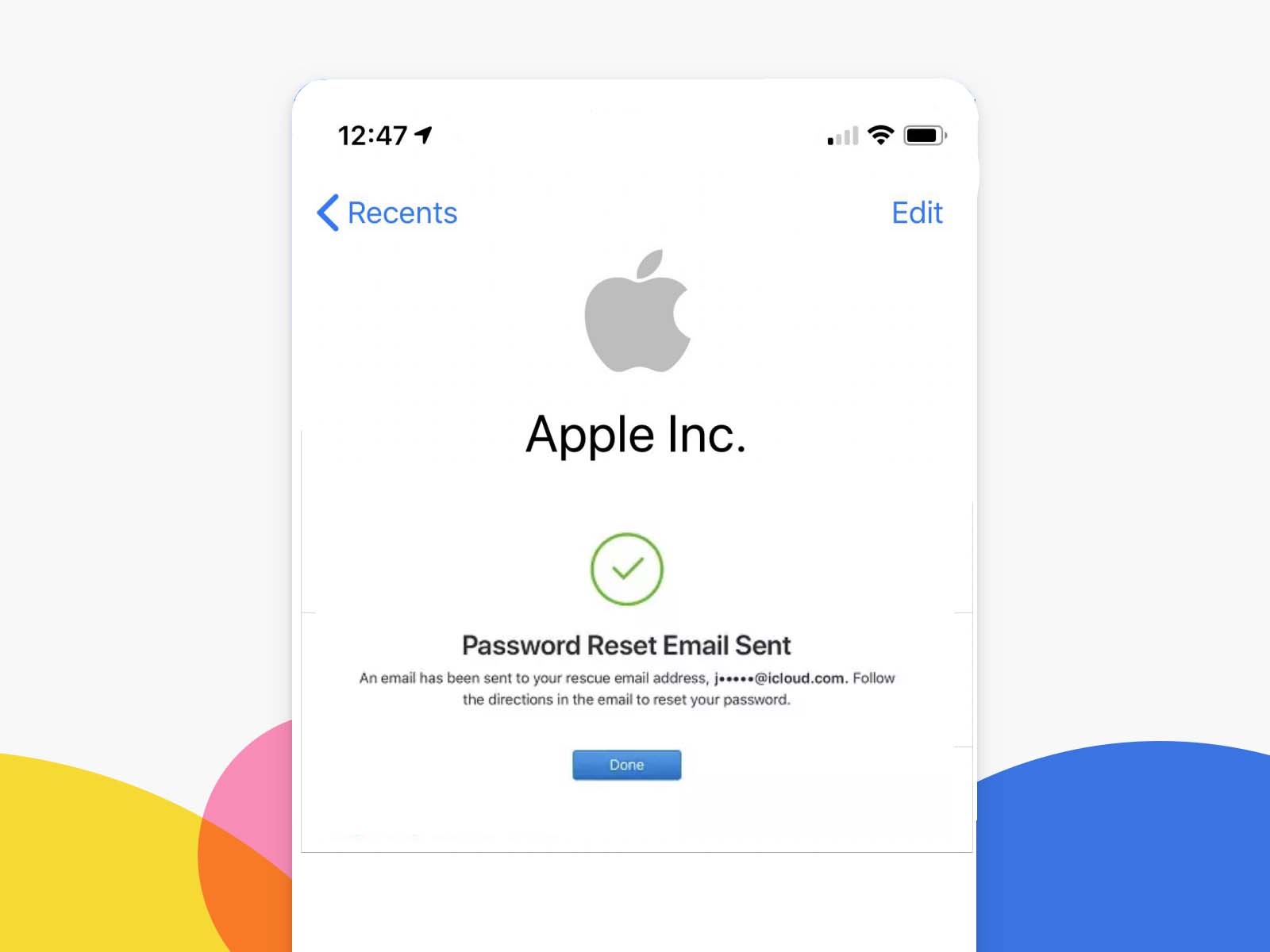
Can I hack ICloud with just my phone number?
Such a possibility exists, and hacking ICloud is possible by intercepting a verification message. The truth is that if you want to spy on iPhones, you need to know their Apple credentials, including the Apple ID or the user's email address.