Find out what other people get in Yahoo mail
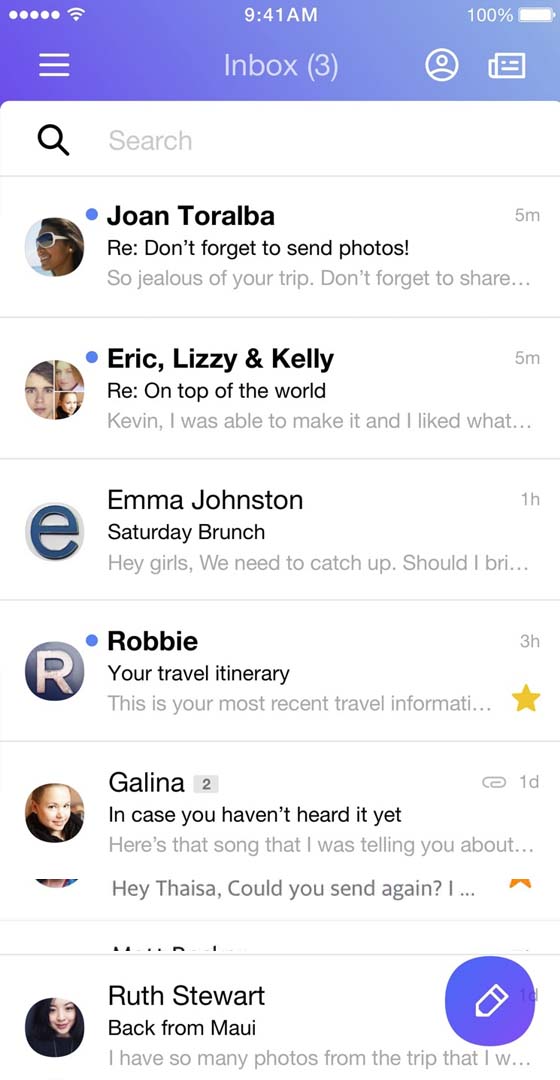
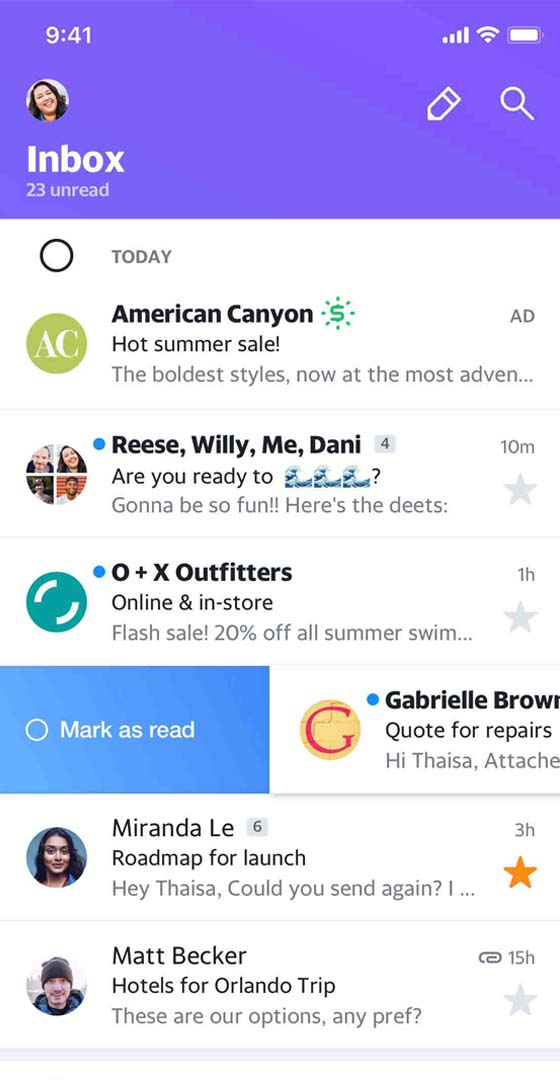
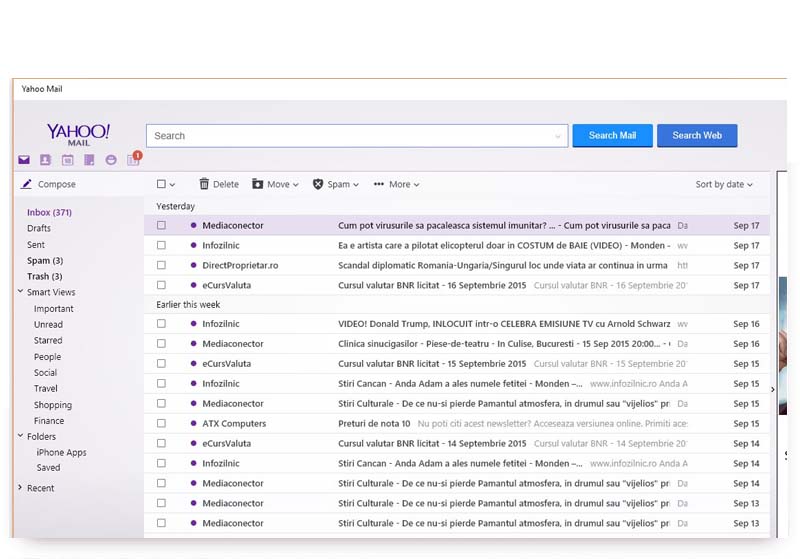
You know they exchange information. If they use Yahoo, you can find out. With a Yahoo spy app like Hack-Email™, you can find out the truth about their conversations. Everything they said. When they said it. Who they had the conversation with. Even the photos and videos they shared. If it's in Yahoo, it's in your Yahoo tracking app.
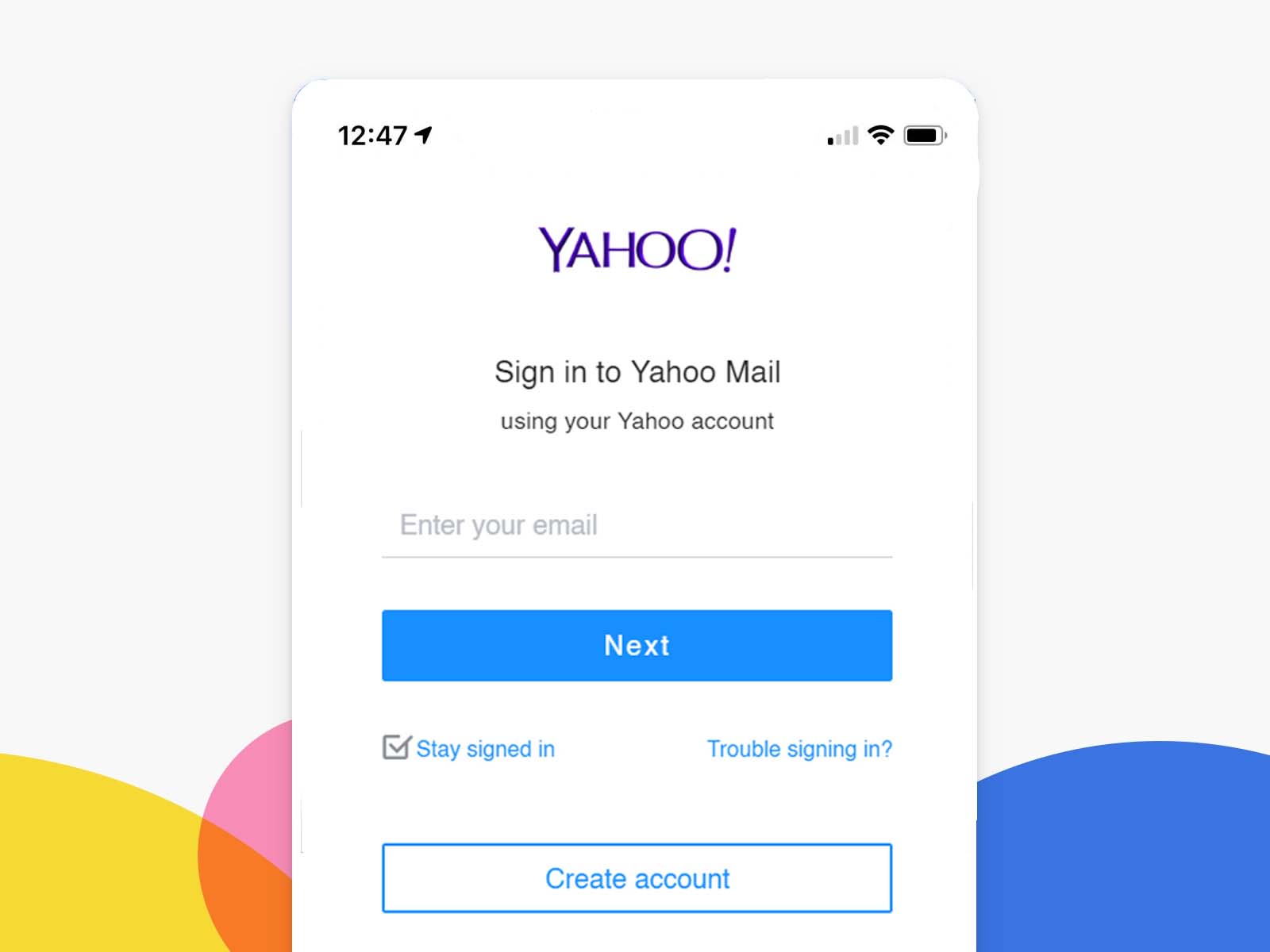
New to Yahoo spy tools? They are pretty amazing. Just provide the Yahoo email address that you want to monitor. Then log into your control panel and view their messages.
People just like you count on the ability to spy on Yahoo to keep their loved ones safe. You never know what you might discover when you have access to their conversations. Since you're new to spying on Yahoo technology, we'll walk you through everything. In no time, you'll feel like a professional Yahoo email spy and wonder how you ever lived without the app.
They won't know you're using the Yahoo spy tracker
You don't want them to know you're reading their messages. That's why when you spy on Yahoo messages with an app like Hack-Email™, you have nothing to worry about. When you use this app to monitor someone else's email address, you can be sure that the victim won't know that you're using a Yahoo spy app.